Alaska's Trusted Cyber Security Experts
Threat Informant was established in 2015 to provide cybersecurity solutions exclusively to the Alaskan market. As a local provider, we are in tune with the needs and challenges of the community, protecting the enterprise from major threats while informing our clients and others with the latest in IT security knowledge.
Advanced Security Research
Our team does extensive research into the latest threats detected, exploits in systems, new malware, and attacker tactics. We leverage that information to protect our customers.
Community Involvement
In 2017, our company decided to start ArcticCon, a local Alaskan IT Security Conference. Working together with the community and other IT organizations to advance IT security education in Alaska.
Applications & Automations
You're an outside-the-box company, so why rely on off the shelf solutions. At Threat Informant, we partner with customers to develop custom applications and automations.
Big Data Analysis & Solutions
Threat Informant specializes in engineering big data solutions and analyzing big data and providing valuable correlations and informations for our clients.
Managed Security
Our main goal is to make sure your company and its data is secure and safe.
LEARN MORE
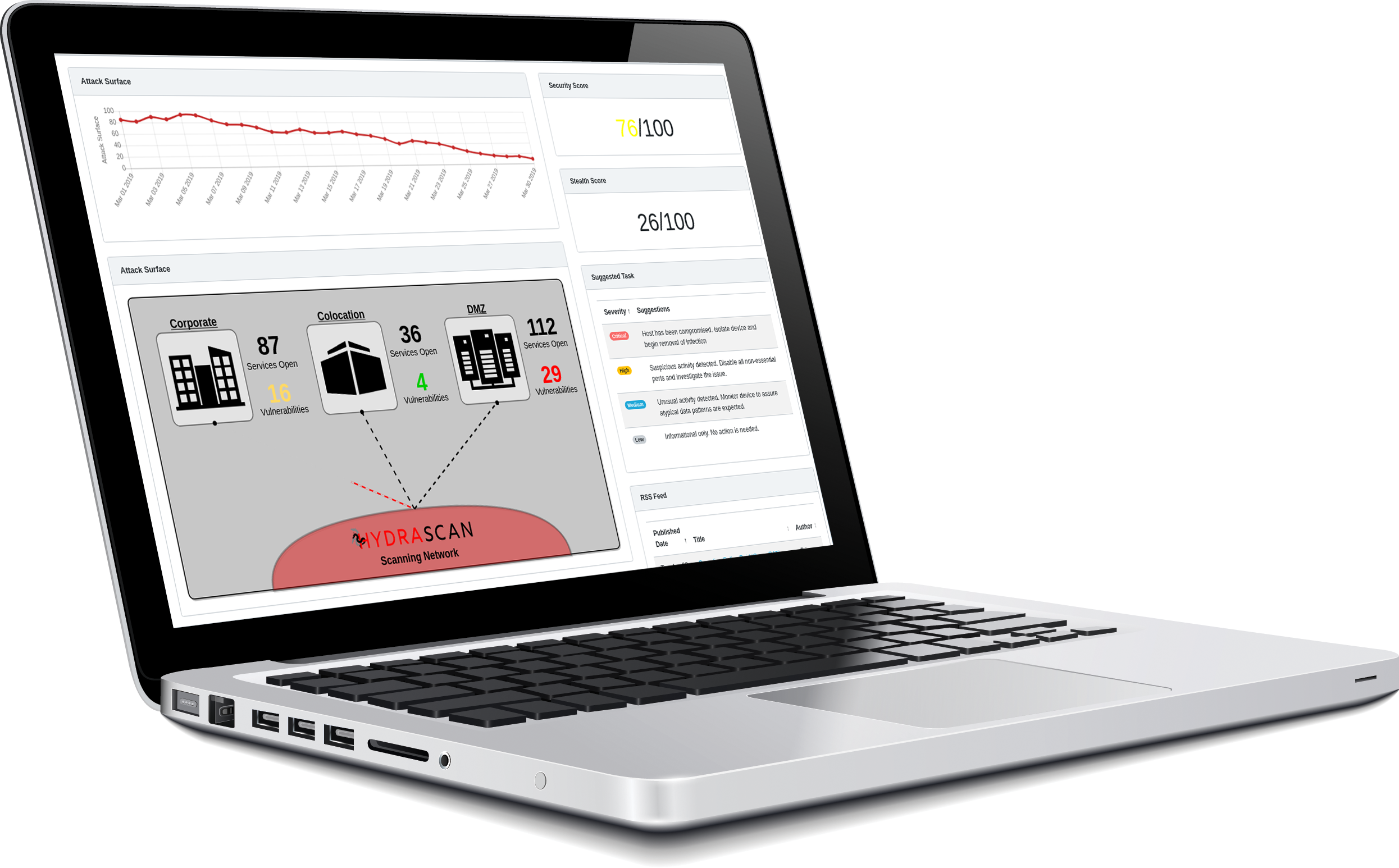
CyberSecurity Management Products
Threat Informant actively engages in advanced security research and develops products based on our findings and our needs that we have discovered while working with our customers. Our two latest releases are Hydrascan and Omnisiem.
Hydrascan tests your defenses like a real attacker. Instead of scanning a real system like a bull in a china shop, Hydrascan executes low and slow discovery scans, designed to bypass traditional security controls to show you what real attackers are seeing.
Learn MoreBusinesses must be constantly vigilant in their defense from outside attackers and malware; small and medium sized businesses being no exception. To properly combat these types of attacks, businesses need to have their logs and data from antivirus software, firewalls, and systems in a secure place, and must have the ability to readily access and analyze this information. Threat Informant developed OmniSIEM to make it easier for business of any size to implement a SIEM solution.
Learn MoreWhat's happening
View the latest post made by our team!
Developing for Clients (the efficient way)
After developing an update, the enduser might have changes they want made or bugs they’ve found. This results in chains of feedback emails between developer... more

- Hannah Cristiano
- Thu, Jun 06, 19
Incident Response Ready
As a trusted advisor to organizations, I often sit in on presentations from other IT security service providers. One phrase that comes up in pretty... more

- Matt Peters
- Sun, Mar 24, 19
Making Splunk frozen data searchable
Splunk is generally our go to tool for data analytics and security incident response. There’s good reasons for that. It’s realtively quick to setup a... more

- Matt Peters
- Mon, Feb 18, 19
Log Management vs SIEM
What’s the difference between Log management and a SIEM? If we’re just breaking down the words Security Information Event Manager, it’s sounds like we can... more

- Matt Peters
- Mon, Jan 28, 19