Hydrascan by Threat Informant
Instead of scanning a real system like a bull in a china shop, Hydrascan executes low and slow discovery scans, designed to bypass traditional security controls to show you what real attackers are seeing.
Evasive Scanning
Hydrascan evades traditional security so you can see your network from an attacker's view
Safe Scanning
Hydrascan executes probes in a slow and random fashion to determine a likelihood of a vulnerability
Human Analysis
After scans have completed, analysts at Threat Informant will manually review the data and submit findings
Common Sense Analysis
Hydrascan learns about what is normal for your network and flags suspicious services for your network
No Assumptions
Unlike other scanners, Hydrascan makes no assumptions and isn’t fooled by simply changing the port
Scan TimeSpan Flexibility
Hydrascan is designed to scan slowly over weeks or months to be safe and stealthy
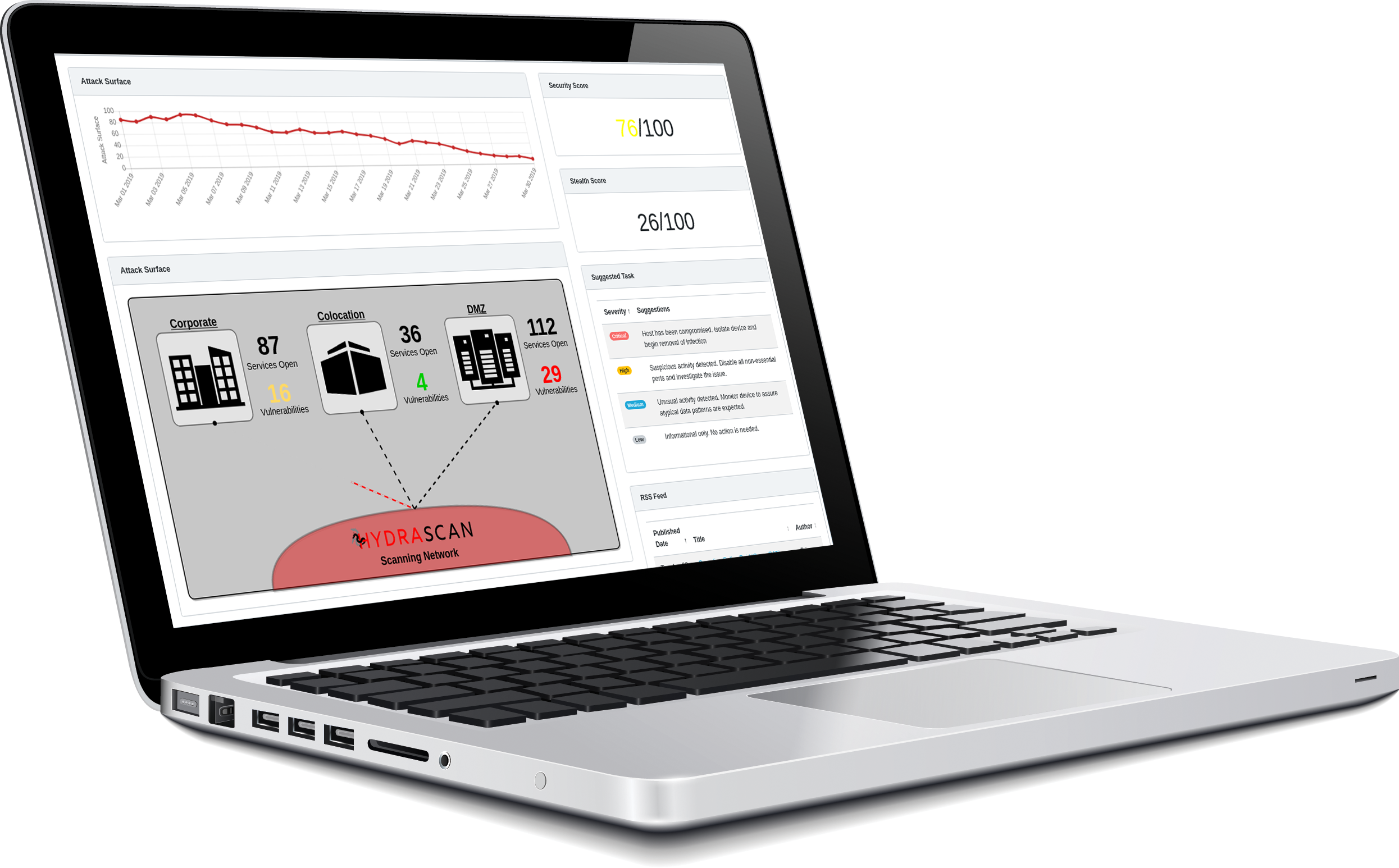
Evasive Scanning
Hydrascan implements measures to probe the network undetected, providing an accurate view of your network from the perspective of an advanced attacker
"Vulnerability scanners typically use port numbers to say which service is which. Hydrascan makes no assumptions and isn’t fooled by simply changing the port number
Human Analysis & Variants
After scans have completed, analysts at Threat Informant will manually review the data and submit findings
Where normal vulnerability scanners look like a bull in a china shop, Hydrascan will execute tests in a slow and random fashion to determine a likelihood of a vulnerability
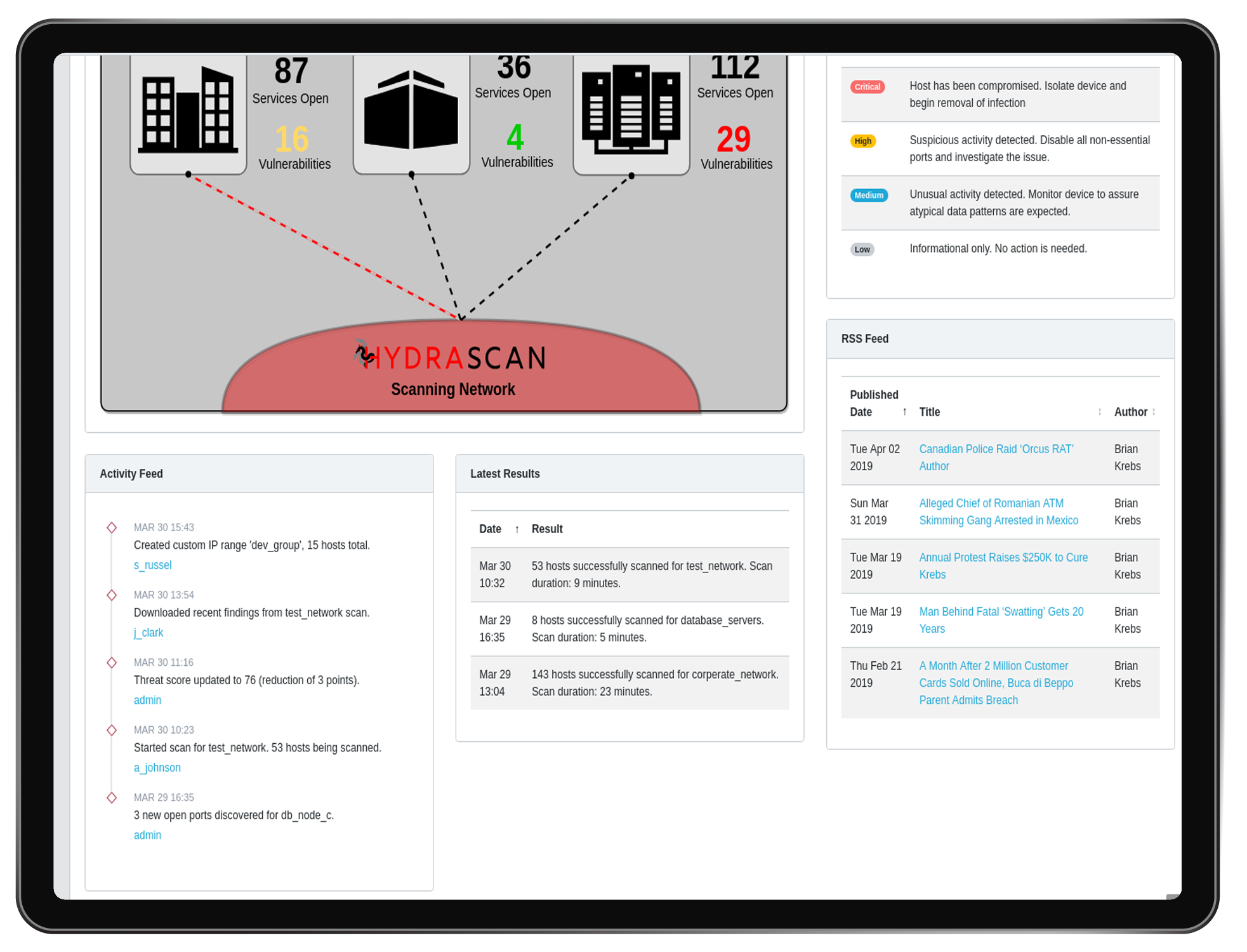
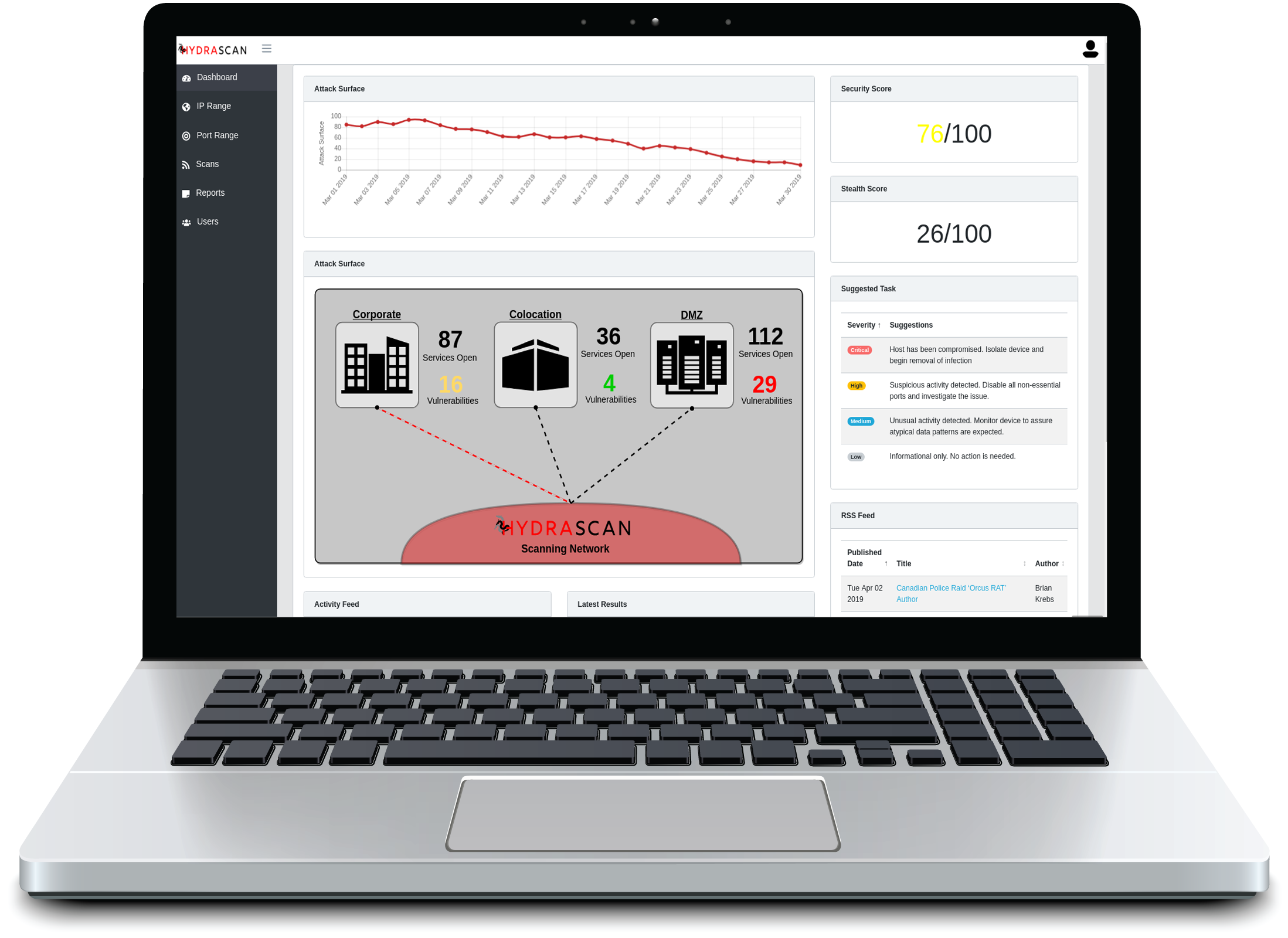
Scan TimeSpan Flexibility
Though Hydrascan can scan much faster than a normal scanner, it is designed to scan slowly over weeks or months to be safe and stealth
Hydrascan learns about what is normal for your network. If most systems seem IPS protected except one RDP service on port 10000, it will flag that as serious.